Online security–Protect your neck
In case you haven’t heard, hackers are slowly taking over the internet. Not really, but you don’t want to accidentally end up in the “lulzy booty” that is collected and distributed daily. LulzSecurity is one very public hacker group quickly becoming (in)famous by attacking websites with weak security and releasing the data they harvest to the wild where they encourage everyone to do whatever they want to with the data. This data includes logins and passwords to various sites and confidential internal company network data. Why are they doing this?? "For the lulz", i.e. just for fun and because they can. This group in particular is growing more and more brazen and has taken down Sony, an FBI affiliate, various professional security consulting companies, random gaming community user databases, the CIA's website, and most recently over 60,000 random email addresses and passwords. They do this while bragging about it and giving the play by play on Twitter (http://twitter.com/#!/LulzSec). The hacker group Anonymous started this recent public trend but they are more focused on real (h)activism not just fun for fame and lulz.
What these guys are doing is not new, but it hasn’t been this public or seemingly random before. This post is aimed at providing some suggestions for securing your public identity on the internet and hopefully help you avoid ending up in one of these public information releases. There are quite a few learning takeaways from the information that has been leaked lately.
Lock down Google
I switched to Gmail many years ago, away from Yahoo and Hotmail, and haven’t looked back. I still hold email accounts on all major mail providers and IMO, none can hold a candle to Gmail in terms of features, functionality, and security. Even if you don't use Gmail then you most likely search Google to find information and may even have a Google account. If you have a Google account, I strongly encourage you to turn on "2-step verification". What this does is ties a phone number, of your choosing, to your Google account. When you attempt to log into Gmail, for example, you will have to input your main password and then a secondary password which will be txt'd or voice called to you. With 2-step verification enabled, even if a hacker were to compromise your Google password they would not be able to log in and get at your information. You can set this so that you only have to do it once per 30 days, not every time you log in.
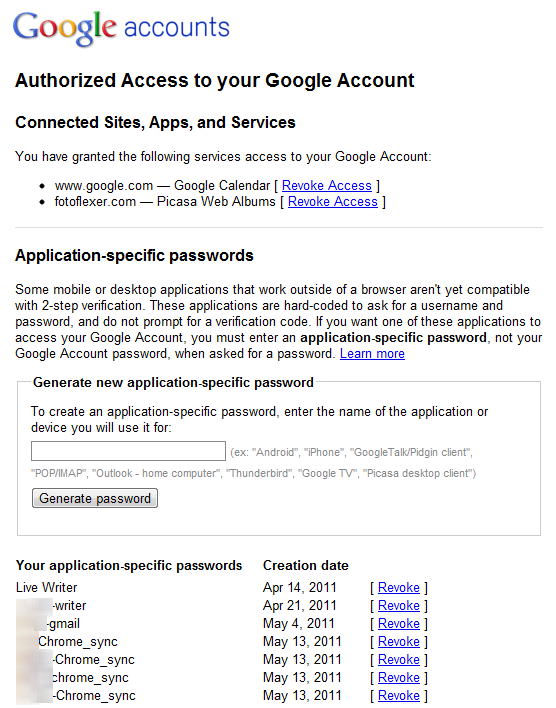
The other advantage this provides is the ability to both authorize and UNauthorize individual computers and applications. For example, let's say you use both Gmail and Chrome Sync on 2 or more computers. You would have to perform this 2-step process on both computers for both Gmail and Chrome sync. Well if for whatever reason you don’t need to use that second computer anymore and you want to kill your Gmail there, or simply want to revoke your Chrome syncs to it. You can simply revoke that individual computer or that individual Google application on that computer!
Google has a nice video and picture section that explains how this works. Seriously, turn it on! http://www.google.com/support/accounts/bin/static.py?page=guide.cs&guide=1056283&topic=1056284
From the Google accounts setting page, click the 2-step verification link and follow the prompts to setup. You will specify a primary + backup phone number and Google will give you some printable backup codes in the event you can’t use phone verification for whatever reason.
The other piece of this is application specific passwords. Any individual application that will need access to any of your Google accounts will have to be expressly authorized. Chrome Sync, blogging tools, etc. These are individually managed with passwords authorizing each one and can in turn be revoked individually.
2-step verification should protect you fairly well in the Google universe but you should also keep an eye on your Gmail account activity. In case you didn’t know, Google tracks and logs the IP address of every public end point you log in from. They will alert you if suspicious activity is detected but I’d still recommend checking this log from time to time to make sure it looks ok. The link is at the very bottom of the Gmail window:
Password reuse
The Anonymous takedown of security firm HBGary proved this to be a BIG problem. People generally use the same password for EVERYTHING! I'd like to say officially and for the record, STOP IT! One of your accounts gets hacked, guess what? They can now log into everything you use online. Facebook, twitter, email, linkedin, your bank maybe, etc. Most people use at least one of the aforementioned services. Save yourself the agony and use a few different passwords depending on the importance of the site. This is how I do it:
- Lastpass - 1 unique password used NOWHERE else, 20+ characters in length.
- Gmail/Google - 1 unique password used NOWHERE else, 12+ characters in length.
- Primary bank - 1 unique password used NOWHERE else, 12+ characters in length.
- Financial (non-bank) - 12+ character reusable password for financial sites ONLY.
- Bills - 12+ character reusable password used only for bill websites.
- Shopping sites – If I have to create an account, I use a throwaway password and allow no credit card info to be stored
- Public sites or offers - throw away password with FAKE email account (dummy gmail/yahoo or mailinator.com)
I encourage you to at the very least separate your important stuff from the not so important stuff. Don't use the same password you use at work for your private email!
Password management
Built-in web browser password managers are ok but not very secure. At least Firefox offers password protection for the password list. There are more secure ways to deal with this if you are so inclined.
A web service that I started using recently is called LastPass http://lastpass.com. This works by installing a plugin into your browser(s) (replacing the built-in password manager), importing your site login info, encrypting it (256-bit AES), then sending the encrypted file to the lastpass servers. The password you use to encrypt the file is never sent to the internet, only a salted hash. There was an incident recently were there was a suspected network attack against lastpass but only accounts using weak passwords were at potential risk. See the note on passwords below. The other advantage lastpass provides is access to all your usernames and passwords from any computer you use.Make sure to use a VERY strong initial password to encrypt your data.
Keepass http://keepass.com is another tool I like to use. This is something you would use on your computer to store and protect various passwords. It creates an encrypted database using the strongest encryption currently known to man (256-bit AES). You could store this at home or use a file sync service like dropbox (dropbox.com) to access it anywhere you go. It's very simple to use and can be had as a portable app to keep in your dropbox for access anywhere. I recommend the pro version of the tool.
Web browsers
How you browse the web is just as important as your passwords and what information you share. My personal recommendation is now officially Google Chrome, a shift away from Firefox. The good news for those of us who are family admins is that Chrome can be installed by all users of a system, even non-administrative users. This means that it can also be updated by non-administrative users, unlike Firefox. Chrome uses a very advanced security mechanism called sandboxing built off of the Windows access token-based security mechanism. This mechanism also isolates each tab and extension in the browser and that tab or extension’s associated files and processes. Flash is baked into the browser (sandboxed) which is automatically updated by Google, another advantage over Firefox. At the most recent hacker convention this year all other major browsers were successfully hacked (IE, Firefox, Safari) while Chrome was not even attempted, even though Google offered an additional $20k cash prize. This could have been due to lack of interest or for fear of the advanced sandboxing. It's also fast and I have yet to see any browser crashes that became routine in even Firefox4. Chrome, get it! http://google.com/chrome
Just like Firefox Chrome has many extensions that increase the functionality of the browser. Chrome does not currently have nearly as extensive the catalog that Firefox does, but they’re getting there. There are 3 extensions that are absolutely mandatory for me: AdBlock, Flashblock, and a script killer. NoScript works great in Firefox but doesn’t exist in Chrome. Luckily there is an alternative called “not scripts” that performs in very much the same way. It blocks all embedded scripts in all websites unless you have given express permission for that site to run scripts (java, flash etc), jscripts, or other potentially damaging web code. Running with a script killer requires a very active user willing to put out a bit more effort to surf the web as each web site you visit will require exceptions for certain elements to run properly. Personally, I wouldn’t surf without it!
*Side note – Chrome can be installed by non-administrative users because it installs into and runs from an individual’s user profile. It does not follow the normally excepted best practice of installing into \program files (Windows) so this creates a potentially challenging situation in the corporate environment. If you are running Windows7/ Server 2008 R2, look into turning on AppLocker which will take care of this problem.
A note on passwords in general
There are many schools of thought when it comes to password policies. As an architect I have the luxury of defining and enforcing these policies for the companies that I work for. Password lengths are always a stated requirement, usually a minimum of 6-8 characters. Sometimes complexity is required by using CAPITALS, numbers and special characters $%#!. Yes, long and complex passwords are more secure but they're also hard to remember. The approach I like to take is longer passwords with no complexity employing a pass-phrase. Something easy for you to remember, for example: howboutthemmavs, or iamahistorybuff. This type of password, due to its length, would take exponentially longer to crack than a shorter 8-character password, even with complexity! Most password crackers only play in the 10 or less character space. Using a longer password removes you from the equation! Now if a given website stores your password with no encryption, this creates a different problem if that database is compromised. This is why limiting password reuse is important.
Limit your exposure
Don't give your information to just any website that requests it! If it's a site you got via email or just stumbled on and just want to check it out, use fake info with a throw away email account. Make use of throwaway email services, my favorite is http://www.mailinator.com . Be mindful of how much of you is already out there. Any of these sites that you log into could fall over and that login info given to the world. Practice anonymity when possible and especially if you don't trust a site. Never use the same password for a highly public site (facebook) and anything else important (gmail/ bank). Opt to not let a shopping site save your credit card number for future use.
Do what the hackers do
Make yourself completely anonymous. TOR is a popular tool used by hackers that proxies your internet requests through various servers all over the world. Your “true” location cannot be sourced because the sites you connect to will only see the address of the proxy. Don’t expect high performance though. You may be relaying through a server in Russia or the UK so browsing can really slow down. If you want to completely hide your tracks from the sites you visit, Tor can help accomplish that goal. http://torproject.org
Wrap up
The moral of the story is to be more careful than you might have been before. Before filling out forms, supplying email addresses etc, be mindful of what you are handing over. Scale back on how much personal info you share on the internet.
- Turn on 2-step verification in your Google account
- Stop using the same username/password for every online account your create!
- Separate your important internet sites from the less important ones by taking steps to isolate and secure the important stuff
- Use an advanced password manager to protect your passwords
- Use longer "pass-phrase" style passwords, 12-characters or longer
- Be mindful of what you sign up for and how much personal information you share on any given site
Stay safe!















No comments: